in 2015, fed up with my lack of technical ability i put life on pause and moved to Thailand to learn programming.
if the nocode movement existed back then, maybe today i’d be the type of guy who makes online communities dedicated to preventing other people from learning to code. and maybe my site would be insecure, leaking all my customers’ private details.
such is the topic of this post.
what follow is a retelling of my first “zeroday” (sort of) finding as a n00b ethical hacker. the target is Bubble.io, but moreso a select few sh*theads who don’t have manners.
here goes!
origin story
my PE fund heard through the grapevine that TinyAcquisitions.com, an online M&A brokerage, was interested in selling their platform.
after checking things out i determined it wasn’t a fit for us, and was about to reply as much. case closed. but then i got bored. maybe their site is hackable?
TinyAcquisitions is powered by Bubble.io, a leading nocode solution. Bubble is sorta like Webflow, with a drag-and-drop website builder except a lot more advanced. you can create databases, 3rd party integrations, etc. in other words you can build entire apps, code-free. i have to give Bubble credit here because the product is super impressive.
anyway. i start clicking around and reviewing network requests, basic security recon. and i notice something. if i visit my own profile, tinyacquisitions.com/profile/ryanckulp, an API request is made here:

so i found another user’s profile, say “/profile/jimbob” (not real), then reconstructed the API request. bingo, the JSON object now has 2 results; my own profile returned from the cookie, and the “profile” slug i’m requesting. this object includes name, email, and a few other fields.
next i developed a PoC (proof of concept) and immediately notified the company. a couple days later my TinyAcquisitions account was suspended and i received a butthurt “you broke the rules” email.
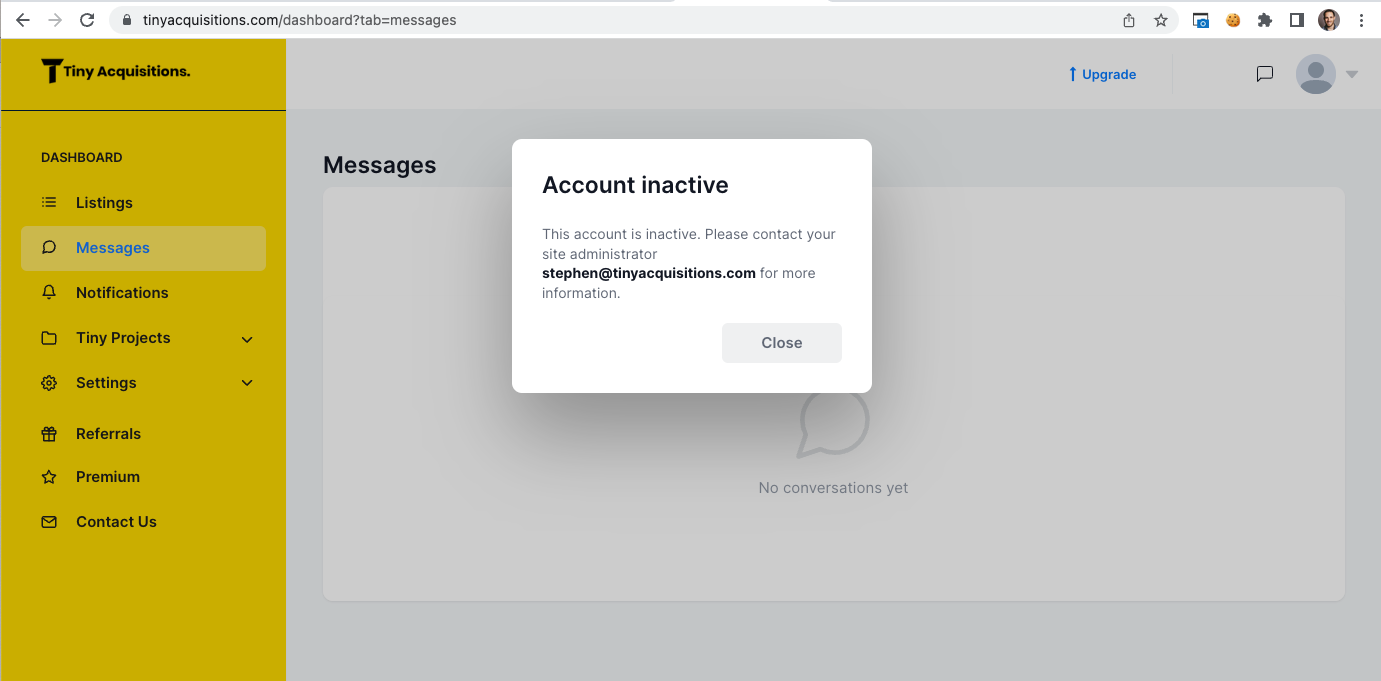
TinyAcquisitions leaked all 14,700 customers’ personal details for months (years?) and instead of saying “thank you,” they scolded me. founder Stephen Campbell is truly a dumbass.
but here’s where things get interesting.
scaling the exploit
i needed to know if this issue was exclusive to TinyAcquisitions, or a vulnerability of Bubble itself.
with simple CLI commands amass enum -d bubbleapps.io and Google query site:bubbleapps.io -www i found 100s of additional Bubble sites to test.
anatomy of the scraper:
- URL + “api/1.1/meta/swagger.json” to find API endpoints
- scan endpoint descriptions for keyword “retrieve a list” (collections)
- hit the endpoints
- parse response JSON for keys like “email:” or “authentication:”
- log results
quickly i found a ton of misconfigured Bubble websites. but before sounding alarm bells on an ecosystem i put on my adult goggles and contacted Bubble directly.
Bubble security program
i emailed Bubble HQ to ask if they have a bug bounty program. unfortunately they do not, but after helping identify security issues on their own website i was credited on the official security page.
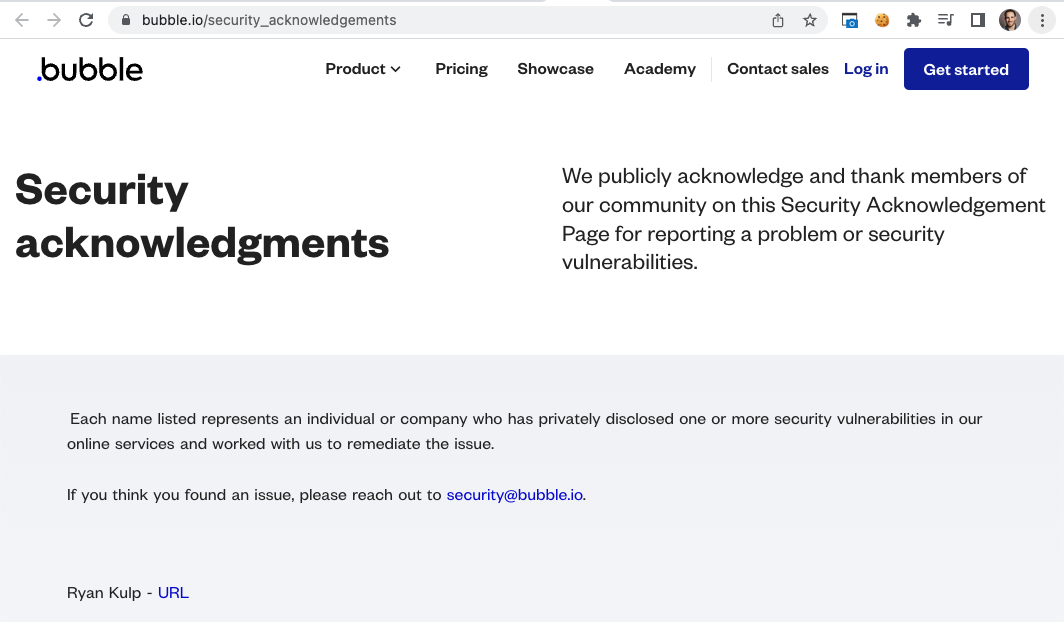
during this process i reasoned Bubble is not responsible for users who mismanage the tools Bubble provides. remember, guns don’t kill people.
with a small W in the pocket, i got back to work on scaling the discovery.
literal growth hacking
one reason i sat on the sidelines of security research for years — besides mistakenly thinking it was too complicated — is that i didn’t see much upside in reporting bugs.
this is not an endorsement for illegal activity. rather, the risk of finding bugs and not being compensated is simply a bad deal.
with this in mind i wanted a better way to report vulnerabilities, a more profitable strategy with higher conversion rates than “look ma, can i get a t-shirt?“
so i pulled out an old tool. one i put away for good years ago — cold email.
the plan? tell Bubble sites their shit is wack and pitch them an eBook to fix it. i wrote the book in a few hours, and TBH it’s great.
next i tapped my buddy Stetson to help scale the operation.
Stetson rebuilt my scraper to test 1000’s of websites, then formatted results into human readable statements like “X with Y email address signed up on Z date.” we merged these sample datapoints into emails like this one.
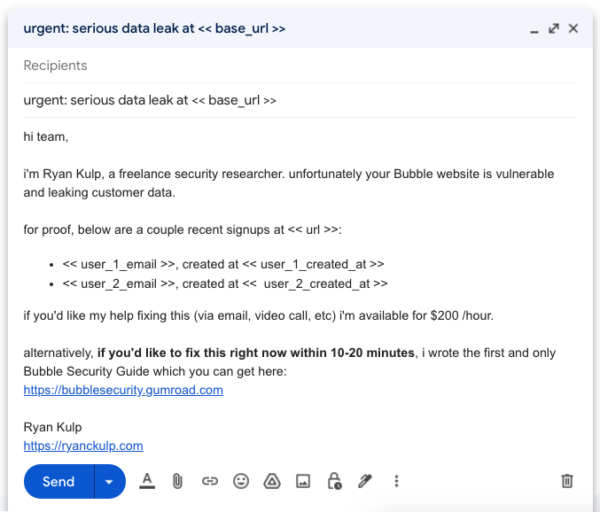
i messaged about 20 companies per day for 3 weeks and got the most conversions on Friday (wonder why hehe). the campaign generated $2,700+ in revenue from a mix of bounties, bonuses, tips, bespoke audit requests, and book sales.
we also spent $249 on a BuiltWith.com license, downloading 23,000 additional Bubble sites to scan.
hall of fame
most of the businesses i informed were appreciative of our work. i will obviously never mention their names or websites.
hall of shame
some “entrepreneurs” opted for the following reactions instead:
- A) ignoring me for weeks, then telling me i’m wrong after* fixing their issue
- B) claiming there is no leak, even after providing additional evidence
- C) never replying, and never fixing their website
a few folks in Group C include PierShare, Tracxn, Premast, and the Gay Men’s Chorus of Washington DC.
my favorite Group A candidate is Salt & Lime, a venture-backed consumer lending company in Australia that was leaking bank statements, drivers licenses, salaries, home addresses, and more. naturally i reported them to the AU government, after which i finally got a playing-dumb reply from founder Will Kiln. incredible stuff.
other marketing tactics
earlier this week i joined a Bubble community on Slack and posted the following self-promotional message, which has already driven 5 more book sales. easy.
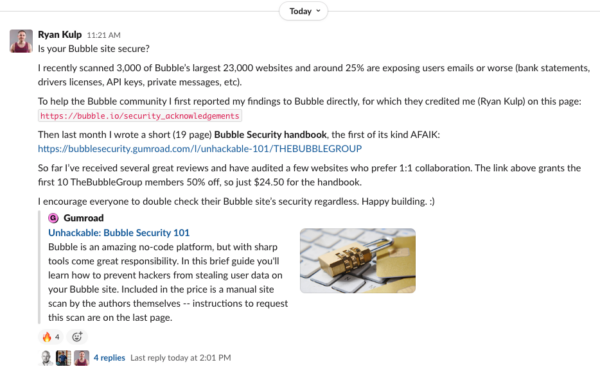
i suppose i could join more Discord, Facebook, Slack communities and let the spamming continue. i could try paid ads or newsletter sponsorships with huge nocode directories and influencers.
but honestly, i’m already bored again. the experiment was a success.
what’s next?
to make things at least a tiny bit challenging for developers reading this post, i’ve omitted a few helpful Bubble API tips. i’m also still sitting on 1000s of vulnerable Bubble websites and founder contact details.
if someone wants to take over the project, try DM-ing me on Twitter.

this is because they didn’t check a box when setting up their API, right?
bubble makes it very easy to miss this config; i don’t think it comes checked by default.